One of the features of the OTRS 5s Security Toolbox is the information floater which allows to search for patterns in an article of a ticket. The feature was designed to enrich the content of a ticket without adding static content to it. Main usage is to give security teams valuable information at a glance without the need to lookup the information in a seperate browser tab.
Out of the box the possibility to search for CVE numbers is available via the Sysconfig settings in Ticket->Ticket::Frontend::ZoomCollectMetaFilters###CVE-Google and Ticket->Ticket::Frontend::ZoomCollectMetaFilters###CVE-Mitre. An additional usecase I had to solve lately was to check weather IP addresses were listed on realtime blackhole lists (RBL).
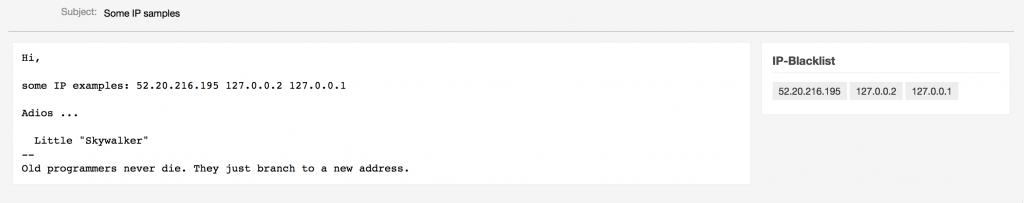
Highlighting IP addresses in the TicketZoom
So first I had to add an additional ZoomCollectMetaFilter which would match on IP addresses. One possible way is to extend the XML which is rendered by the Sysconfig as already described in several posts (e.g. even more RSS feeds in SysConfig). This time I directly created a perl config file “Kernel/Config/Files/ZZZIPCheck.pm” which contains the needed configuration:
$Self->{'Ticket::Frontend::ZoomCollectMetaFilters'}->{'IP-Blacklist'} = {
'Meta' => {
'Name' => 'IP-Blacklist',
'Target' => '_blank',
'URL' => 'dnsrb.pl?ip=<MATCH1>',
'URLPreview' => 'dnsrbl.pl?ip=<MATCH1>',
},
'RegExp' => [
'(\\d{1,3}\\.(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3}))'
]
};
If an IP address is found in an article the references will be displayed in the ticket zoom:
The Perl script
Next step is to create a perl cgi script in the bin/cgi-bin folder of the OTRS installation named dnsrbl.pl:
#!/usr/bin/perl
use strict;
use warnings;
use CGI qw(:standard);
use Net::RBLClient;
my $bl = ['ix.dnsbl.manitu.net','zen.spamhaus.org','b.barracudacentral.org','all.s5h.net','dnsbl-1.uceprotect.net','virbl.dnsbl.bit.nl','proxies.blackhole
s.easynet.nl','cbl.abuseat.org','blackholes.easynet.nl','relays.bl.kundenserver.de','agobot.bl.kundenserver.de'];
my $rbl = Net::RBLClient->new(
lists => $bl,
max_time => 5,
timeout => 1,
query_txt => 1,
max_hits => 10,
server => '8.8.8.8',
);
my $ip = param('ip');
print header(-type => 'text/html',
'X-FRAME-OPTIONS' => 'SAMEORIGIN');
print start_html(-title =>'IP Blacklist Check',
-style=>{'src'=>'//cdn.jsdelivr.net/bootstrap/3.3.7/css/bootstrap.min.css'});
print '<div class="container">';
print '<div class="well">';
print h1("Checked IP: $ip");
print '</div>';
my $result = $rbl->lookup($ip);
my @listed_by = $rbl->listed_by;
my @listed_hash = $rbl->listed_hash;
my @listed_txt = $rbl->txt_hash;
foreach my $list (keys @listed_by){
print '<div class="alert alert-danger" role="alert">';
print '<h4>';
print b($listed_by[$list],": ");
print p($listed_hash[$list]," ");
print i($listed_txt[$list]," ");
print '</h4>';
print '</div>';
}
if (! @listed_by) {
print '<div class="alert alert-success" role="alert">';
print '<h3>';
print 'IP not found on blacklist';
print '</h3>';
print '</div>';
}
print '</div>';
print end_html;
As the script uses the Net::RBLClient class it has to be installed first. I used CPAN:
root@otrs:/opt# cpan
cpan[1]> install Net::RBLClient
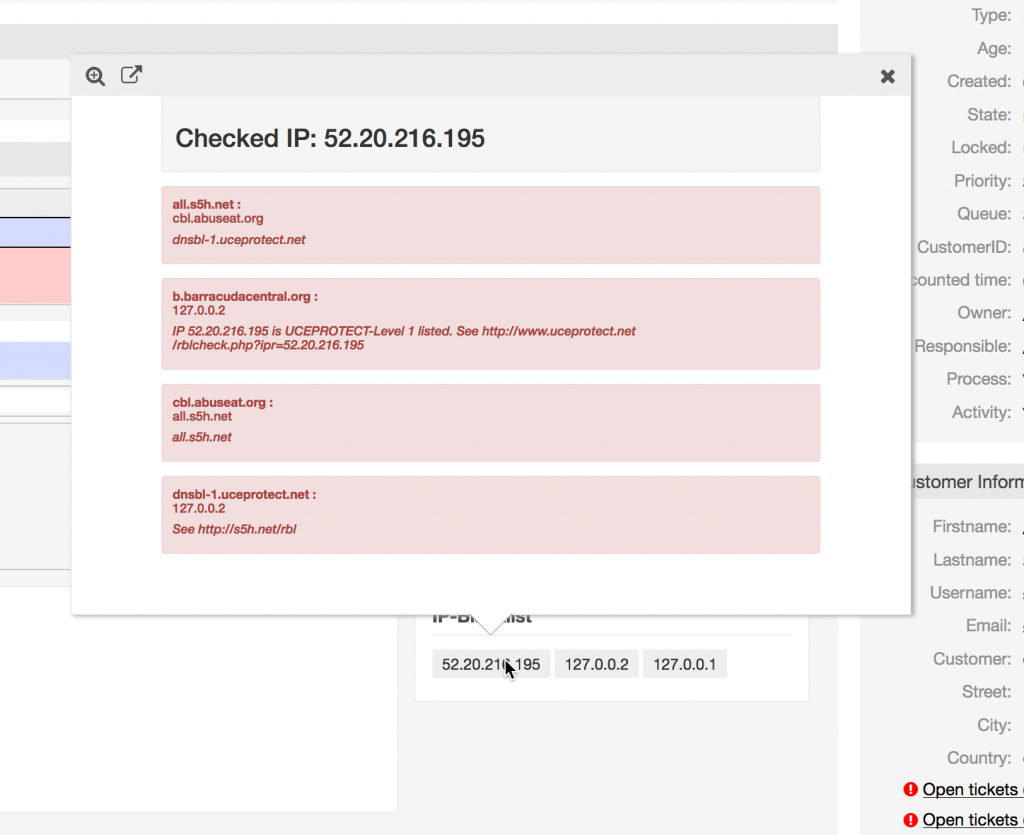
Floater Output
The floater now will lookup the ip address in the configured RBL and render the page
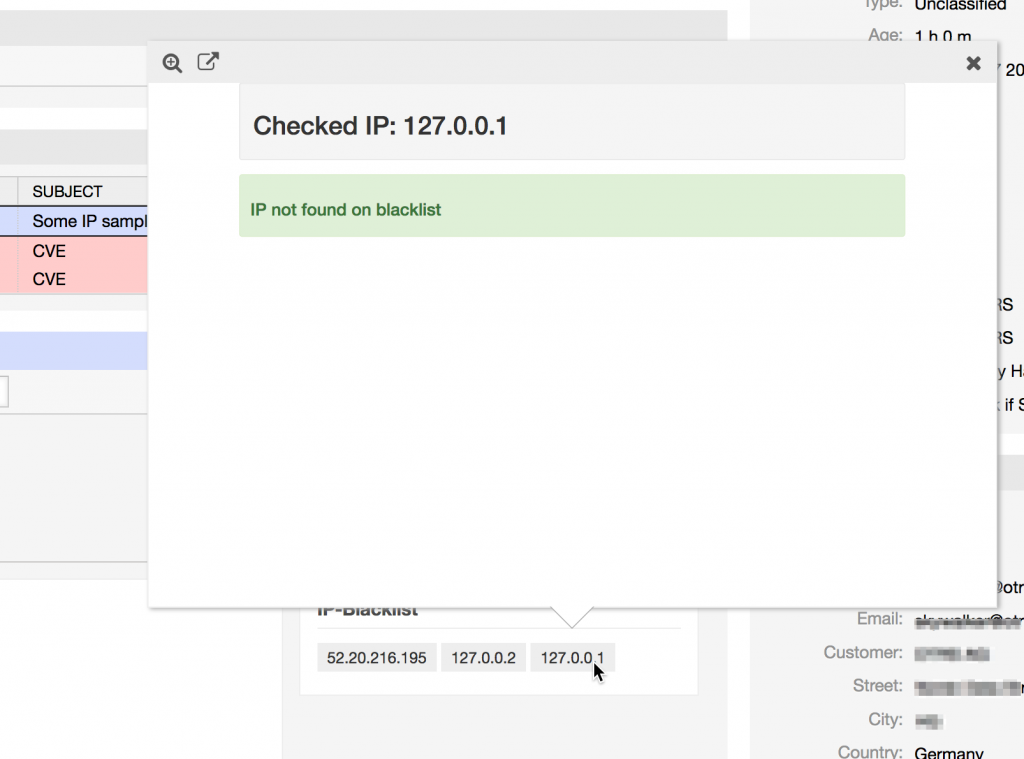
Or if no match is found
I really would like to see your usecases and ideas to use the Information Floater of the OTRS 5s so please leave a comment.
The post Checking IP reputation via Information Floater appeared first on The OTRS Blog.